Compare commits
6 Commits
| Author | SHA1 | Date | |
|---|---|---|---|
| bed54826d6 | |||
| b318bcb3c1 | |||
| 390fabe1b4 | |||
| 92f5c579e6 | |||
| 305ba29c50 | |||
| f8be95c8d0 |
4
.gitignore
vendored
4
.gitignore
vendored
@ -3,4 +3,6 @@ hyp.secret
|
|||||||
hypd/hypd
|
hypd/hypd
|
||||||
hyp/hyp
|
hyp/hyp
|
||||||
hypd/hypdconfig.json
|
hypd/hypdconfig.json
|
||||||
hypd/secrets/
|
hypd/secrets/
|
||||||
|
hypd/server/*.o
|
||||||
|
env.sh
|
||||||
|
|||||||
@ -1,6 +1,6 @@
|
|||||||
# hyp | Hide Your Ports
|
# hyp | Hide Your Ports
|
||||||
|
|
||||||
[](https://drone.deadbeef.codes/steven/hyp)
|
[](https://drone.deadbeef.codes/steven/hyp)
|
||||||
|
|
||||||
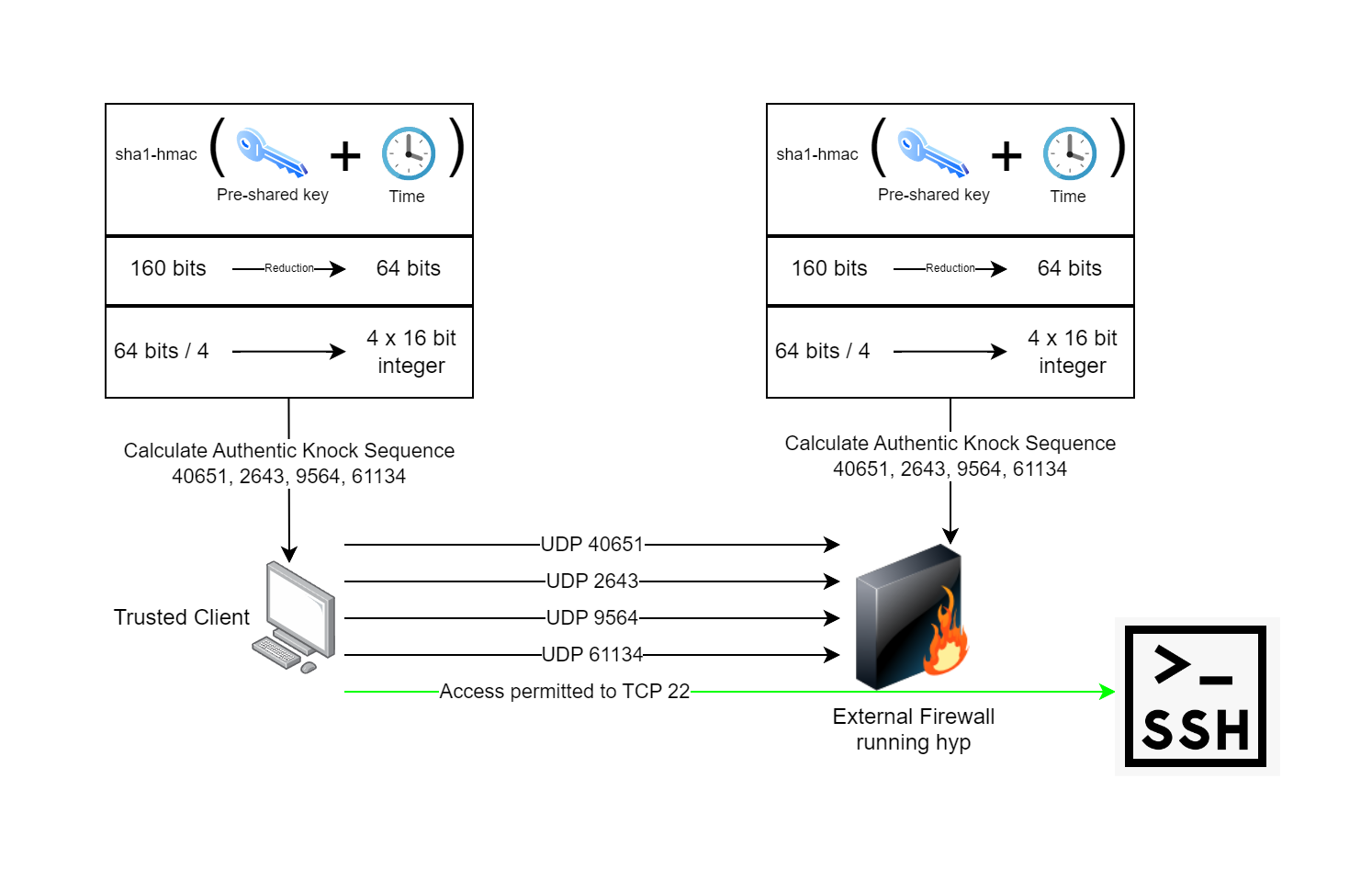
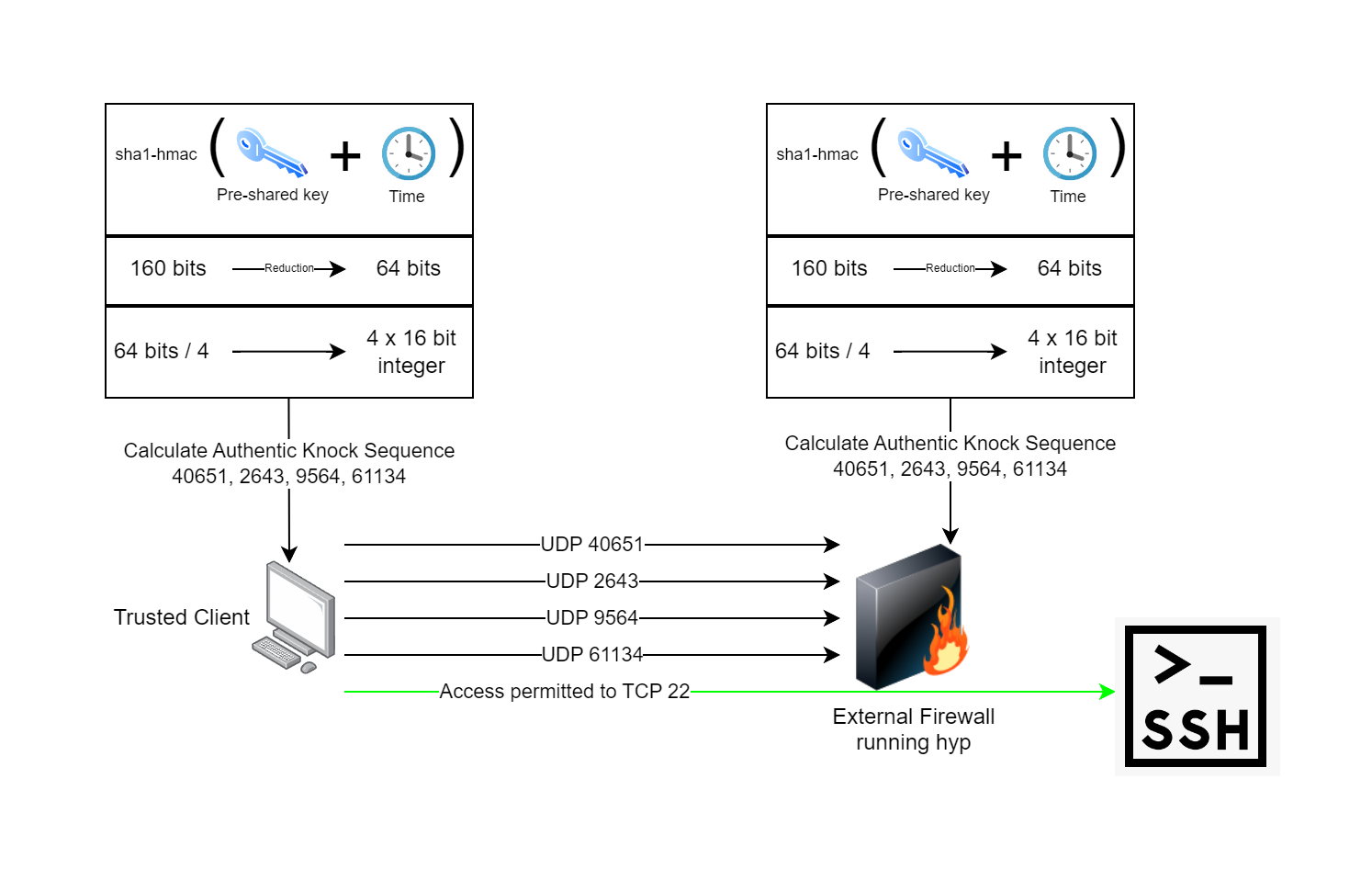
hyp is a [port knocking](https://www.youtube.com/watch?v=a7VJZEJVhD0) implementation written in Go and C. hyp uses spread-spectrum UDP as an authentication mechanism and enables trusted agents to access services over the internet, wherever they are, and without the service being accessible by others. Your TCP and UDP ports are closed. They will not show in a port scan. Nobody else can connect to them. This is particularly useful as [there](https://nvd.nist.gov/vuln/detail/CVE-2024-21888) [have](https://nvd.nist.gov/vuln/detail/CVE-2023-20269) [been](https://nvd.nist.gov/vuln/detail/CVE-2021-26109) [a](https://nvd.nist.gov/vuln/detail/CVE-2024-22394) [few](https://nvd.nist.gov/vuln/detail/CVE-2024-21894) [VPN](https://nvd.nist.gov/vuln/detail/CVE-2024-3400) [gateway](https://nvd.nist.gov/vuln/detail/CVE-2023-27997) [vulnerabilities](https://nvd.nist.gov/vuln/detail/CVE-2024-21762) [over](https://nvd.nist.gov/vuln/detail/CVE-2022-3236) [the](https://nvd.nist.gov/vuln/detail/CVE-2024-21893) [years](https://nvd.nist.gov/vuln/detail/CVE-2022-42475). I often wonder what's out there and hasn't been discovered. Why take the chance of leaving your VPN open to the whole internet? With hyp, you don't have to.
|
hyp is a [port knocking](https://www.youtube.com/watch?v=a7VJZEJVhD0) implementation written in Go and C. hyp uses spread-spectrum UDP as an authentication mechanism and enables trusted agents to access services over the internet, wherever they are, and without the service being accessible by others. Your TCP and UDP ports are closed. They will not show in a port scan. Nobody else can connect to them. This is particularly useful as [there](https://nvd.nist.gov/vuln/detail/CVE-2024-21888) [have](https://nvd.nist.gov/vuln/detail/CVE-2023-20269) [been](https://nvd.nist.gov/vuln/detail/CVE-2021-26109) [a](https://nvd.nist.gov/vuln/detail/CVE-2024-22394) [few](https://nvd.nist.gov/vuln/detail/CVE-2024-21894) [VPN](https://nvd.nist.gov/vuln/detail/CVE-2024-3400) [gateway](https://nvd.nist.gov/vuln/detail/CVE-2023-27997) [vulnerabilities](https://nvd.nist.gov/vuln/detail/CVE-2024-21762) [over](https://nvd.nist.gov/vuln/detail/CVE-2022-3236) [the](https://nvd.nist.gov/vuln/detail/CVE-2024-21893) [years](https://nvd.nist.gov/vuln/detail/CVE-2022-42475). I often wonder what's out there and hasn't been discovered. Why take the chance of leaving your VPN open to the whole internet? With hyp, you don't have to.
|
||||||
|
|
||||||
@ -14,7 +14,7 @@ Compared to most port knocking daemons, hyp is extremely fast, lightweight and h
|
|||||||
6. The knock daemon on the firewall verifies the sequence and performs the action of opening the firewall port configured for the client to let them in while remaining closed to everyone else.
|
6. The knock daemon on the firewall verifies the sequence and performs the action of opening the firewall port configured for the client to let them in while remaining closed to everyone else.
|
||||||
7. The client connects to their application which has its own authentication, authorization, and auditing.
|
7. The client connects to their application which has its own authentication, authorization, and auditing.
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
### Runtime Requirements
|
### Runtime Requirements
|
||||||
|
|
||||||
|
|||||||
7
hypd/examples/fortigate/hypdconfig.json
Normal file
7
hypd/examples/fortigate/hypdconfig.json
Normal file
@ -0,0 +1,7 @@
|
|||||||
|
{
|
||||||
|
"networkInterface": "enp0s3",
|
||||||
|
"preSharedKeyDirectory": "./secrets/",
|
||||||
|
"successAction": "./examples/fortigate/openfortigate.sh %s",
|
||||||
|
"timeoutSeconds": 0,
|
||||||
|
"timeoutAction": ""
|
||||||
|
}
|
||||||
33
hypd/examples/fortigate/openfortigate.sh
Executable file
33
hypd/examples/fortigate/openfortigate.sh
Executable file
@ -0,0 +1,33 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
|
||||||
|
# Make sure you have environment variables set for FORTIGATE_MGMT_URL, FORTIGATE_API_TOKEN and FORTIGATE_ADDRESS_OBJECT_GROUP
|
||||||
|
# Examples:
|
||||||
|
export FORTIGATE_MGMT_URL="https://69.4.20.10:8443"
|
||||||
|
export FORTIGATE_API_KEY="5fkwkkzgQ4s31bdH60qsxxfN093zgt"
|
||||||
|
export FORTIGATE_ADDRESS_OBJECT_GROUP="hyp-allowed-clients"
|
||||||
|
|
||||||
|
|
||||||
|
if [ $# -lt 1 ]; then
|
||||||
|
echo "Usage: $0 <srcip>"
|
||||||
|
exit 1
|
||||||
|
fi
|
||||||
|
|
||||||
|
echo $FORTIGATE_MGMT_URL
|
||||||
|
echo $1
|
||||||
|
|
||||||
|
# Create the address object
|
||||||
|
curl "$FORTIGATE_MGMT_URL/api/v2/cmdb/firewall/address?datasource=1" \
|
||||||
|
-X "POST" \
|
||||||
|
-H "Authorization: Bearer $FORTIGATE_API_KEY" \
|
||||||
|
-H "Content-Type: application/json" \
|
||||||
|
--data-raw "{\"name\":\"hyp_$1\",\"subnet\":\"$1/32\",\"color\":\"0\"}" \
|
||||||
|
--insecure # LOL - remove this if you want, but I want this to be easy for noobs
|
||||||
|
|
||||||
|
|
||||||
|
# Add to address object group
|
||||||
|
curl "$FORTIGATE_MGMT_URL/api/v2/cmdb/firewall/addrgrp/$FORTIGATE_ADDRESS_OBJECT_GROUP/member" \
|
||||||
|
-X "POST" \
|
||||||
|
-H "Authorization: Bearer $FORTIGATE_API_KEY" \
|
||||||
|
-H "Content-Type: application/json" \
|
||||||
|
--data-raw "{\"name\":\"hyp_$1\"}" \
|
||||||
|
--insecure # And here too
|
||||||
12
hypd/examples/openwrt-wireguard/README.md
Normal file
12
hypd/examples/openwrt-wireguard/README.md
Normal file
@ -0,0 +1,12 @@
|
|||||||
|
# Using hyp with OpenWrt Wireguard
|
||||||
|
|
||||||
|
This example case is to deploy hypd on OpenWrt to open up access to the WireGuard VPN service.
|
||||||
|
|
||||||
|
hyp utilizes eBPF technology to ensure runtime overhead is extremely small (in a way, but in a way not). Most Linux distributions have support for this out of the box, however OpenWrt does not. OpenWrt has a very stripped down, purpose-configured kernel and does not have the requirements built in to run hyp.
|
||||||
|
|
||||||
|
The good news is, you can build OpenWrt yourself and configure it with the requirements. Follow the directions at this page: https://openwrt.org/docs/guide-developer/toolchain/use-buildsystem
|
||||||
|
|
||||||
|
When you run *make menuconfig*, make sure you check off *Enable additional BTF type information* which is also known as CONFIG_KERNEL_DEBUG_INFO_BTF. This is required to support eBPF CO:RE.
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
BIN
hypd/examples/openwrt-wireguard/kernel_config.png
Normal file
BIN
hypd/examples/openwrt-wireguard/kernel_config.png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 148 KiB |
@ -35,32 +35,40 @@ int xdp_prog_func(struct xdp_md *ctx) {
|
|||||||
|
|
||||||
// A knock should not contain any data
|
// A knock should not contain any data
|
||||||
if (data_end - data > 60) {
|
if (data_end - data > 60) {
|
||||||
goto done;
|
return XDP_PASS;
|
||||||
}
|
}
|
||||||
|
|
||||||
// parse ethernet header
|
// parse ethernet header
|
||||||
struct ethhdr *eth = data;
|
struct ethhdr *eth = data;
|
||||||
if ((void *)eth + sizeof(*eth) <= data_end) {
|
if ((void *)eth + sizeof(*eth) > data_end) {
|
||||||
// parse IP header
|
return XDP_PASS;
|
||||||
struct iphdr *ip = data + sizeof(*eth);
|
|
||||||
if ((void *)ip + sizeof(*ip) <= data_end) {
|
|
||||||
if (ip->protocol == IPPROTO_UDP) {
|
|
||||||
// parse UDP header
|
|
||||||
struct udphdr *udp = (void *)ip + sizeof(*ip);
|
|
||||||
if ((void *)udp + sizeof(*udp) <= data_end)
|
|
||||||
{
|
|
||||||
// pack into knock structure and send to userspace
|
|
||||||
struct knock_data knock = {
|
|
||||||
.srcip = bpf_ntohl(ip->saddr),
|
|
||||||
.dstport = bpf_htons(udp->dest),
|
|
||||||
.pad = 0
|
|
||||||
};
|
|
||||||
bpf_ringbuf_output(&rb, &knock, sizeof(knock), BPF_RB_FORCE_WAKEUP);
|
|
||||||
}
|
|
||||||
}
|
|
||||||
}
|
|
||||||
}
|
}
|
||||||
done:
|
|
||||||
|
// parse IP header
|
||||||
|
struct iphdr *ip = data + sizeof(*eth);
|
||||||
|
if ((void *)ip + sizeof(*ip) > data_end) {
|
||||||
|
return XDP_PASS;
|
||||||
|
}
|
||||||
|
|
||||||
|
// Ensure IP header protocol field is UDP (protocol 17)
|
||||||
|
if (ip->protocol != IPPROTO_UDP) {
|
||||||
|
return XDP_PASS;
|
||||||
|
}
|
||||||
|
|
||||||
|
// parse UDP header
|
||||||
|
struct udphdr *udp = (void *)ip + sizeof(*ip);
|
||||||
|
if ((void *)udp + sizeof(*udp) > data_end) {
|
||||||
|
return XDP_PASS;
|
||||||
|
}
|
||||||
|
|
||||||
|
// pack into knock structure and send to userspace
|
||||||
|
struct knock_data knock = {
|
||||||
|
.srcip = bpf_ntohl(ip->saddr),
|
||||||
|
.dstport = bpf_htons(udp->dest),
|
||||||
|
.pad = 0
|
||||||
|
};
|
||||||
|
bpf_ringbuf_output(&rb, &knock, sizeof(knock), BPF_RB_FORCE_WAKEUP);
|
||||||
|
|
||||||
// We send everything to XDP_PASS
|
// We send everything to XDP_PASS
|
||||||
return XDP_PASS;
|
return XDP_PASS;
|
||||||
}
|
}
|
||||||
|
|||||||
Binary file not shown.
Binary file not shown.
Loading…
Reference in New Issue
Block a user